Send payloads over a Network with Scapy (unfinished)
Scapy, originally developed in Python by Philippe Biondi, is a tool that allows users to easily create and manipulate a network packet. For this project I’ll demonstrate how to create a simple packet with a string payload and send it to a selected IP or MAC address. I’ll break down the code and demonstrate how to find your packet in WireShark.
Installation
Scapy works best with Unix based systems, but newer versions can be run on Windows. If you’re using a programming oriented Virtual Machine such as Kali Linux or Red Hat Linux, it’s likely scapy is preinstalled. Type “scapy” into cmd/terminal to check. If the Scapy Interface doesn’t appear it can be installed in the following ways:
Mac and Windows
best way
(replace “basic” with “complete” to get Scapy + extensions)
pip install --pre scapy[basic]
GitHub install
git clone https://github.com/secdev/scapy.git
linux and Mac with Brew
wget https://github.com/secdev/scapy/archive/master.zip
$ unzip master.zip
$ cd master
Type “scapy” into terminal/cmd and you should see the Scapy user interface come up:
To send one packet use scapy’s send() function:
send()
We’re going to create an IP packet so we’ll use the IP() function. The IP() function’s parameters take in the packet’s destination: An IP address or MAC address can be passed into dst=””
send(IP(dst="192.168.7.32"))
and optionally a “source” from which the packet will appear to come from. This lets you spoof the packet source, but you won’t receive a response packet as it will go to the spoofed source.
send(IP(dst="192.168.7.32", src="118.244.221.56"))
For now I’m not going to use src=”” as I want to receive a response packet. Next, specify what network protocol you want to use. I’m going to use TCP protocol, but scapy let’s you use a range of network protocols such as ICMP() and UDP().
send(IP(dst="192.168.7.32")/TCP())
And finally attach a payload to your packet. To keep things simple I’ll attach a string:
send(IP(dst="192.168.7.32")/TCP()/"Hello!")
Launch the packet and head over to WireShark.
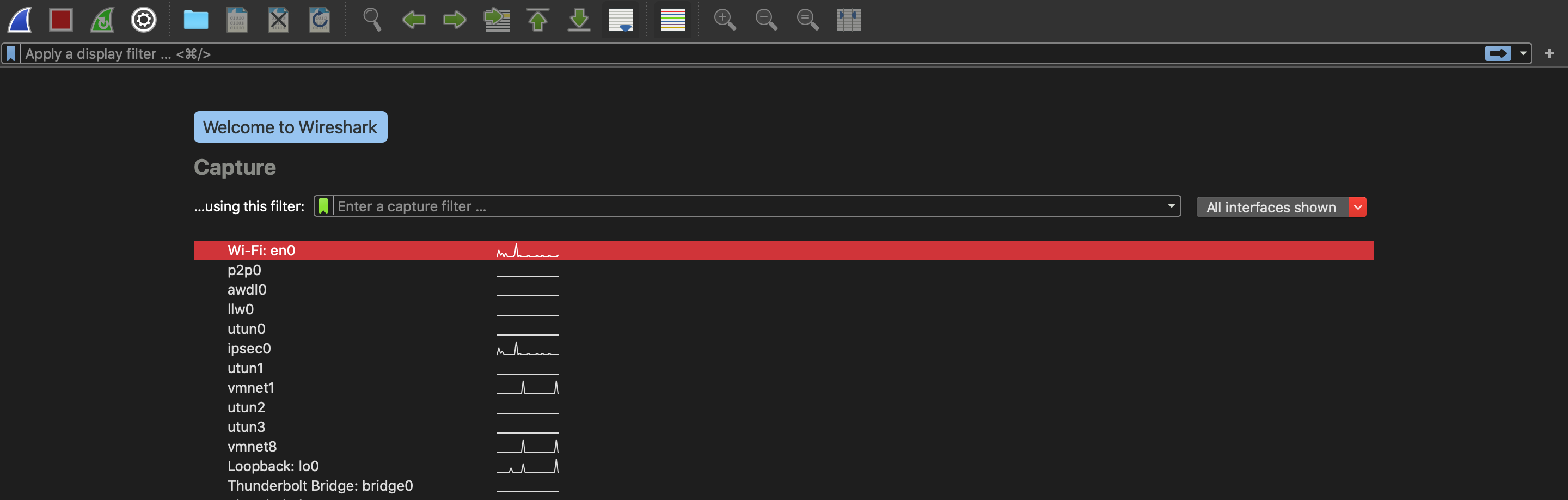
Now you’ll have a number of network interfaces to choose from, but LAN, Wifi(en0), and ethernet(eth0) interfaces are usually the only networks with real activity. I’m not running a Virtual Machine so it’s likely my packet will travel over Wifi. If you’re using a Virtual Machine it will travel over a wired network (with the exception of a wireless adapter). Go to the Wifi interface and sort by TCP packets or IP address ip.dst==192.168.7.32 (or both: ip.dst==192.168.7.32 and tcp). After sorting by tcp for a bit I found my packet:
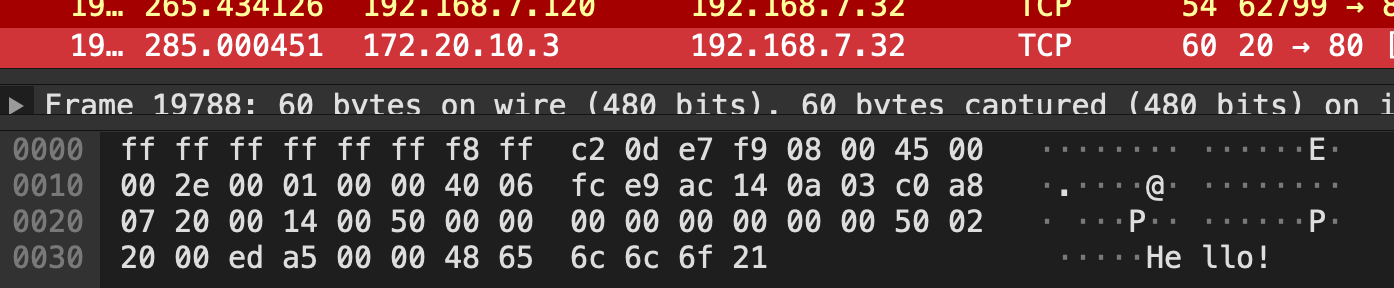
Looking at the packet’s hex may be a bit intimidating at first, but Wireshark can interpret it (most of it) for you after capturing the packet. Near the end you can see our added payload: “Hello!”.